Multiple Ways to Banner Grabbing
Grabbing a banner is the first and apparently the most important phase in both the offensive and defensive penetration testing environments. In this article, we’ll take a tour to “Banner Grabbing” and learn how the different command-line tools and web interfaces help us to grab the banner of a webserver and its running services.
Table of Content
- Introduction
- Why Banner Grabbing?
- Types of Banner Grabbing
- Banner grabbing using Kali Linux
- whatweb
- cURL
- wget
- telnet
- netcat
- Nikto
- Nmap
- Dmitry
- Banner grabbing over Burpsuite
- Banner grabbing using Netcraft
- Banner grabbing through Browser Extensions.
- Wappalyzer
- HTTP Header Live
- Banner grabbing using ID Serve
Introduction
“Banner Grabbing” is often termed as “Service Fingerprinting”.
Banner refers to a text message received from the host, usually, it includes information about the open ports and services with their version numbers.
Why Banner Grabbing?
Banner Grabbing allows an attacker to discover network hosts and running services with their versions on the open ports and moreover operating systems so that he can exploit the remote host server.
Banner Disclosure is the most common vulnerability with a “CWE-200 i.e. Exposure of Sensitive Information to an Unauthorized Actor” and a “CVSS Score of 5.0 with the Risk factor as Medium.”
In order to clear the vision, we’ll consider an attack scenario:
As we all know that Microsoft Windows 7 are exploitable by Eternal Blue (CVE-2017-0143) directly with SMBv1 service. In order to enumerate this server, the attacker needs to grabs a service banner which displays whether the SMB service with a vulnerable version is running over it or not. If running, he/she can easily exploit the Microsoft server directly with the Eternal Blue attack. You can learn more about this attack from here.
Types of Banner Grabbing
- Active Banner grabbing –In this, the attacker craft or modify his/her own packets and send them to the remote host server and analyses the response data in order to get the operating system information and the services running with their versions.
- Passive Banner grabbing –Here the attacker collecting data about our target using publically available information i.e. by analyzing the server either with the help of “Error Messages” or by “Sniffing up the Network Traffic”.
Up till now, you might have gained a lot of information about what is Banner Grabbing and why it is used?
Let’s continue this journey by exploring the most aggressive and direct methods of grabbing a service banner.
Banner grabbing using Kali Linux
Whatweb
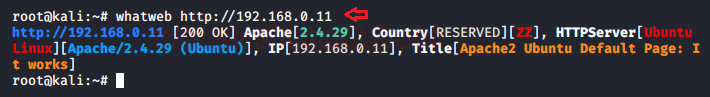
“WhatWeb” recognizes websites, which helps us to grab the web-applications banner by disclosing the server information with its version, the IP address, the webpage Title and running operating system.
Type the following command in order to capture the essentials.
whatweb <website URL>
whatweb http://192.168.0.11
cURL
The cURL command includes the functionality for retrieving the banner details from HTTP servers. Just execute the following command, and discover what we grab:
curl –s –I 192.168.0.11
However to fetch a clean result, we are using the -s flag to prevent the progress of the error messages from being displayed, and the -I flag to simply print out the header information of all requested pages.

Wget
We will be using the wget command to capture the HTTP banner of the remote server.
wget –q –S 192.168.0.11
The –q flag will cover-up the progress of our output, while the -S flag will print out the header information of all requested pages.

Telnet
We will be using the Telnet protocol in order to interact with services to grab their banners.
Type following command to grab the FTP banner of the remote server.
telnet 192.168.0.11 21
As a result, it will dumb “220 (vsFTPd 3.0.3)”

Netcat
Netcat is a network utility that will again help us to grab the FTP banner of the remote host server.
nc 192.168.0.11 21
From the above image, you can check that it dumbs up “220 (vsFTPd 3.0.3)”

Nikto
Nikto is an open-source web-application scanner, which we’ll be using to grab a banner of a website running on an Ubuntu server.
Type the following command in order to capture the installed web server – its version, the configuration index files, the HTTP server options and a list of other useful details.
nikto –h http://192.168.0.11
The –h flag is used to specify the host.

Nmap
We’ll use Nmap as a simple banner grabber which connects to an open TCP port and prints out anything sent by the listening service within a couple of seconds
Type following command which will grab banner for the SSH service running on port 22 in the remote host.
nmap -sV –p22 192.168.0.11
The -sV flag prints out the version of the running service.
From the above screenshot, you can read the SSH service and its version, fetched by NMAP as “OpenSSH 7.6p1 Ubuntu 4ubuntu0.3”

Dmitry
Dmitry (Deepmagic Information Gathering Tool) has the ability to gather as much information as possible about a host. Base functionality is able to gather possible subdomains, email addresses, uptime information, tcp port scan, whois lookups, and many more.
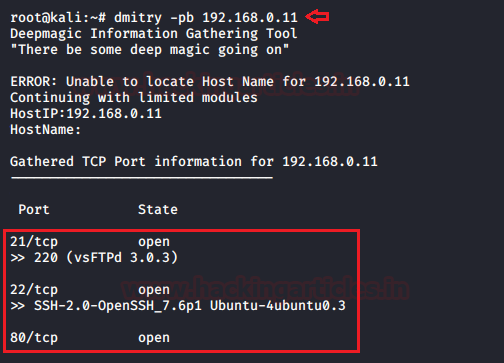
The –pb flag is used to grab the banner for all the open-ports of the remote host.
Fire the following command to grab the banners of the running services.
dmitry –pb 192.168.0.11
Banner Grabbing over Burpsuite
While performing an attack or a penetration test, we all use burp suite somewhere or the other, but does it help us to identify the target’s web server?
Yes, we can simply grab the server’s information through the response generated by the repeater.
From the below screenshot you can see that I’ve sent the interpreted request into the repeater. As soon as I hit the send button, the response will be executed and on the right-hand side you will get the captured server details as Apache/2.4.29 (Ubuntu)

Banner Grabbing using Netcraft
Netcraft is one of the most operatable information gathering web-interface which help us to check the technologies and the infrastructure of the web-applications.
So I’ll be using a demo website over Netcraft in order to grab some service banners and capture all the possible information.
From the above image, you can see that I have grabbed the Hosting History of testphp.vulnweb.com, which shows up the IP addresses, the operating systems and the webservers along with their last seen.

Banner Grabbing through Browser Extensions
Sometimes it’s a bit time consuming while grabbing banners of multiple web applications. Thus in order to make our work faster, we will be setting up some browser extensions that will help us to capture the server information with their version numbers, the running operating systems and the other frameworks that drive up the web applications.
Wappalyzer
Wappalyzer is a free browser extension available for both Mozilla Firefox and Google Chrome. It helps us to check the technologies of the web-application, majorly the server with its version and the framework running on it. You can add this extension in your browser from here.

From the above image you can see that, we have easily captured “Apache 2.2.0” as the server, “PHP 5.3.10” as the programming language and “Ubuntu and Fedora” as the running operating systems.
HTTP Header Live
This extension gives us the power to capture the ongoing HTTP Requests before they are sent to the server.
Therefore we are going to garb some server banners through this HTTP Header extension. You can add it in your browser from here.
From the below image you can see that, as soon as I capture the HTTP request, I was presented with the target’s information containing the server and the operating system banners i.e. Apache/2.4.29 (Ubuntu)

Banner Grabbing using ID Serve
ID Server is a free and a general-purpose Internet server identification utility which helps us to grab the banner of a remote host. You can download the tool from here.
Just enter the target’s website URL and hit the “Query This Server” button. And there it goes, it dumps everything it could, including the IP addresses, open ports, cookie and the server information.

Author: Chiragh Arora is a passionate Researcher and Technical Writer at Hacking Articles. He is a hacking enthusiast. Contact here
Hello sir , if you have a time , write some articles about web app pentesting reports , and thanks for your beautiful and awesome articles .